 |

 IBM-AUSTRIA - PC-HW-Support 30 Aug 1999
IBM-AUSTRIA - PC-HW-Support 30 Aug 1999 |
Security (3546)
Security
The Dock II has two features to secure it from
being used by unauthorized persons.
Security Lock
The security lock is located on the left panel of the
Dock II and can be unlocked with the security lock key. This
security lock provides the following protection:
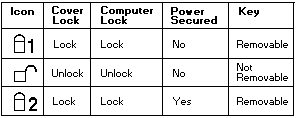
- Cover Lock prevents unauthorized access
to the devices and options inside the Dock II.
- Computer Lock protects from unauthorized removal of
the computer.
- Key Controlled Power prevents
unauthorized use of the Dock II or unauthorized access to
the data stored on the
internal SCSI device through the external
SCSI connector by securing the power.
The key lock has three positions.
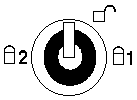
Security Hole
A hole for the Kensington lock is located at the rear of the Dock II.
The cable on the Kensington lock is looped around a stable chair or a
similar item and the Kensington lock is attached to the hole at the rear
of the Dock II. This prevents the Dock II to be carried away by an
unauthorized person.
Back to 
More INFORMATION / HELP is available at the IBM-HelpCenter
Please see the LEGAL - Trademark notice.
Feel free - send a  for any BUG on this page found - Thank you.
for any BUG on this page found - Thank you.
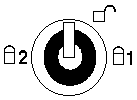

 for any BUG on this page found - Thank you.
for any BUG on this page found - Thank you.